Surviving the pandemic has tested everybody’s powers of endurance. For individuals, and for enterprises everywhere, it has been a troubling and disruptive time. For many businesses it has been a matter of adapting at light speed to ensure survival. It has also seen several tectonic shifts at the level of IT, either accelerating trends that were already in progress or creating fresh waves, the implications of which still unfolding.
“Firstly there was a shift towards the cloud and enterprise digitalization as people dispersed to work remotely,” notes Mauricio Sanchez, Research Director, Network Security & Data Center Appliance, SASE Market Research, Dell’Oro Group. “We saw enterprises that hadn’t necessarily been particularly digital, as far as their clients and workers were concerned, suddenly having to dial that in. Then there was the conversation about every business’s online digital experience from a security perspective.”
It was an uncertain time even for seasoned security practitioners, he says: “Then this summer, ransomware hits the front pages with companies like Colonial Pipeline getting hit hard by a massive outage of their facilities. More recently we’ve seen Russia’s Yandex suffer one of the largest DDoS attacks in history. Cyber threats weren’t slowed down by the pandemic. In fact, they have probably accelerated in many respects.”
Figure 1: Out with the old

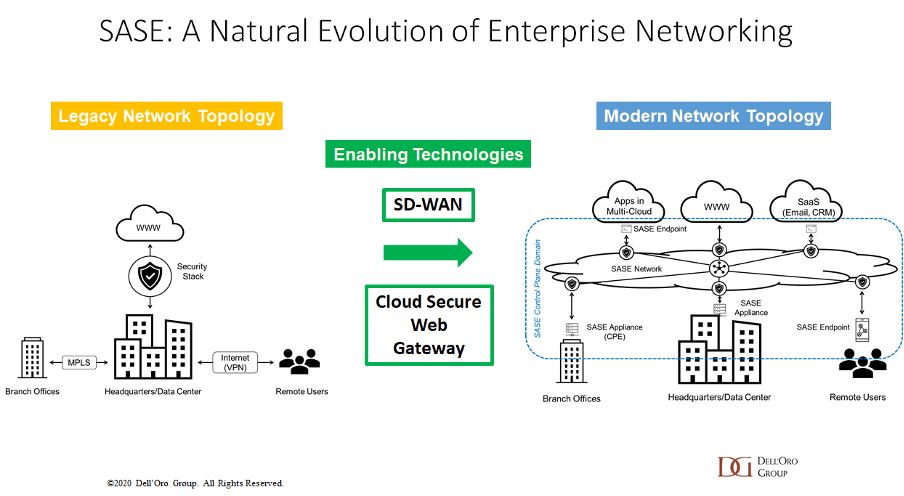
Changes in working patterns, in tandem with a rising tide of security threats, forced a lot of enterprises to think about their reliance on legacy network architecture, believes Sanchez: “The classic hub and spoke model that has worked for many decades was in doubt. It was a tried and trusted model, good at protecting the inside of the corporate network, with everything backhauled to that data center at the heart. A lot of enterprises have started to understand that this architecture no longer fits what’s needed, and that’s led to a new class of architecture solutions matched by some new enabling technologies.”
Not least of these has been SASE, or the secure access service edge: “We see this as the next wave in networking,” claims Sanchez. “The vendor community has responded to enterprise pressure with this intersection of networking and security, by providing a converged networking and security solution.”
Figure 2: SASE – a natural evolution
So what, wonders Sanchez, are the top security threats enterprises facing today? To help answer this he spoke to a panel of seasoned security professionals from around the world of commerce.
Gail Coury, Senior Vice President and Chief Information Security Officer with security vendor F5 Networks, sees the challenge as multi-faceted: “At F5 we have moved so many of our applications out of our data centers,” she says. “One of our top goals is to be completely out of that business. If you look at how our workers do their work today, remotely from their home offices, they are very rarely getting on a VPN. But now we have an expanded attack surface, with some applications still in an on-premise data center, others protected by SASE, many in multiple clouds around the world helping us manage our employees and support our customers. We see threats to applications, threats to the end user, threats to the devices users are connecting from.”
Attackers are busily adapting to the new defensive measures that everyone is putting in place, believes Jordan LaRose, Director of Consulting and Incident Response with security vendor F-Secure: “We have new technologies to stop classical attacks, like ransomware,” he says. “It’s funny that I’m saying ransomware is classical, as it’s only been around for a couple of years. But that’s how quickly the industry is moving nowadays. I’d add that ransomware attackers are not just targeting computers anymore, they also target key servers, key users on the network, exfiltrating intellectual property, or blackmail information, or anything they see as valuable that they can take and base a ransom on. They’ll hold it hostage and say if you don’t pay us this money we’re going to leak this information to the public Internet. This is a big challenge for the industry because protection now needs to target the entire network.”
There’s a need, he says, for the tech industry to increase security even more, to cover not just an enterprise’s ‘crown jewels’, but also to make sure that nothing unintentional goes in or out: “So not just your key database, but your CFO’s laptop that he’s got sitting on his desk at home in Florida.”
The nature of today’s highly distributed organisations makes the job of security much harder, notes Vivek Bhandari, Sr. Director of Product Marketing, Networking and Security Business Unit with VMware. “Apps are everywhere, users are everywhere, we have all kinds of devices,” he says. “Architectures are fundamentally changing with containerized applications, and with so many components spread across multiple clouds. It has created a field day for attackers because now the attack surface has exponentially grown. It’s become so much easier now for attackers to find their way in.”
Another source of worry for Bhandari is the area of Zero Day exploits: “Compared to the last two years, in 2021 alone we have seen more than two times the use of Zero Day exploits in the wild. This is something for which a lot of traditional security defences, that rely on signatures or known behavior, can’t react to. It’s like somebody with a mask on masquerading as something they are not.”
Dr Ronald Layton, Vice President, Converged Security Operations with Sallie Mae Bank, wants to see budgets for security expand in line with those for other tech services: “Law enforcers should adopt a more collaborative approach, just like we do in the private market where we’ll pick the phone up and call a friend who’s the CISO and ask what they are seeing,” he says. “We are all better when we collaborate, and the bad actors have picked this up rapidly. They’ve always been effective collaborators on the offensive side, better than on the defensive side which is where we all play.”
Coury of F5 Networks finds it useful to leverage her experience as the former head of a business facing multiple security headaches: “Before I took the role of CISO at F5, I was general manager for one of our online security services business where we were protecting hundreds of customer environments against DDoS attacks,” she explains. “DDoS-as-a-service is something that the hackers have gone into. I also want to mention bot traffic and credential stuffing traffic that is focused on applications.”
So what are the solutions out there that enterprises should be thinking about, in the face of all these fast evolving threats?
Bhandari of VMware is a believer in Zero Trust as a paradigm: “What we’re beginning to see is organizations start thinking of securing end user traffic with solutions like SASE and ZTNA,” he says. “Look at all the stuff that’s happening within the cloud and across clouds, with almost every organization now shifted to a multi-cloud strategy where applications are hosted. We have to secure workload access as well, and it’s not only about user access.”
Coury of F5 Networks wants more done to integrate security: “I’m talking about API security, and how micro services connect to each other. How do you secure the data? The data itself should be independently protected. How do you secure the user, how do you have positive strong identity, and then how do you make sure you authenticate the device? You must know that device is healthy before you allow that connection to occur, and this is all because we don’t have that perimeter anymore. This is why we have to change the way we think about security.”
By way of conclusion, LaRose of F-Secure notes that he always says to clients who are either in the middle of or recovering from a cyber-attack, there is no silver bullet for security.
“There’s no one piece of software that’s going to solve all of your problems,” he concludes. “I wish there was, it would make my job a lot easier. But, unfortunately, it’s all about understanding all of the different levels of technology, all the different levels of risk, and identifying the right solution for each one of those individual pieces.”
By Guy Matthews, Editor of NetReporter
Featured Speakers:
Analyst Chair: Mauricio Sanchez, Research Director, Network Security & Data Center Appliance, SASE Market Research, Dell’Oro Group
www.delloro.com
Gail Coury, Senior Vice President and Chief Information Security Officer, F5 Networks
www.f5.com
Jordan LaRose, Director of Consulting and Incident Response, F-Secure
www.f-secure.com
Dr. Ronald Layton, Vice President, Converged Security Operations, Sallie Mae Bank
www.salliemae.com/banking
Vivek Bhandari, Sr. Director of Product Marketing, Networking and Security Business Unit, VMware
https://www.vmware.com/







Responses